Forkbomb
So, originally I asked my employees a question: "What was your most salient line of code?" and one of them came up with a very clean solution. We are planning a re-run as soon as the servers are up and running again, and I shall be personally responsible for the restart.
Introduction
A forkbomb is a script code or a compiled binary code programmed to multiply (fork), usually uncontrollably, leeching all Central Processing Unit's (CPUs) resources until it's dead.
History
Although the forkbomb origins can be traced back to as far as the '60 of the 20th century, to the general public, it was immortalized in a Twitter discussion in the spring of 2022 by one of the Dunder Init's employees, it was a response to the CEO's Friday ."Question of the Week". What started as a dark humour born of an exhausted mind became a turning point in history. The CEO, enchanted by the sheer elegance of the code, decided to try it out in the console, frying his CPU fragments of seconds later.
How is the damage done?
General information
Forkbomb relies on mass replication of the processes and can be easily stopped by limiting the number of processes a single user can run at a given time. Since every process chips a bit of the Computer Processing Units (CPU) processing power, the forkbomb eats away all of the resources until none are left, and the CPU crashes.
Neat examples
An elegant example was once written in a bash script:
:() { :|:& }; : # Don't run it! It will crash your computer!
The one-liner above can be broken down into three distinct parts:
- define a function named ":" which takes no arguments
- call the function and run the second one in the background
- run the function
What is it used for?
In the old days, it was used for Denial of Service hacker attacks when a vulnerable system, e.g. a server, would run the forkbomb, causing it to crash. Nowadays, with the process limiting implemented virtually everywhere, it appears only in software engineering jokes. But there is an urban legend, according to which people with actual administrator credentials have fallen for the trick to quench their curiosity by testing the code.


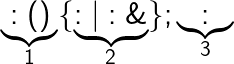

The attribution of that quote had me giggling--as did the rest of the article with the "in the old days" notes sprinkled here and there. Great job! :D
You are doing a great job! Keep creating; I believe in you!
Luridity: Where love is love and life is lived. Contains NSFW content.
Now with serialized fiction on Ream!!
Thank you, Dani! I'm glad you enjoyed it!